I’ve recently been playing through Deus Ex: Human Revolution. I’ve been enjoying it so much that I’m virtually certain that there’ll be a replay of the original Deus Ex in my near future.
I’ve recently been playing through Deus Ex: Human Revolution. I’ve been enjoying it so much that I’m virtually certain that there’ll be a replay of the original Deus Ex in my near future.
One of the really great features in both titles is your ability to hack dozens or hundreds of computer terminals throughout the game, revealing data – from the variety of electronic communications you eavesdrop upon – that can provide you with valuable operational intel, deeper insight into the conspiracy, and access to unique resources.
This kind of “information in depth” works wonders in terms of immersing you into the game world; it’s also a lot of fun. But replicating this kind of experience in a tabletop RPG is really difficult: Even if you don’t go so far as to prep individual handouts for every e-mail and chat log the PCs uncover, it would still require an almost insane amount of prep work in order to customize the contents of the dozens of computer terminals in a typical complex.
To solve this problem, I’ve thrown together a simple-to-prep game structure for tactical hacking. This system assumes a couple of things are generally true: First, the hacker is opportunistically targeting systems to compromise. Second, the primary goal of the hacker is to accrue information. (The structure includes some minimal support for other hacking strategies, but they’re not the primary focus of the structure.)
For the sake of simplicity, I’m going to assume a D20-style system with a single Hacking skill. But it should be fairly easy to modify these guidelines for any RPG with discrete action checks.
NETWORKS
Each network is defined by a Network Intel Table (NIT). Each entry on the NIT is a discrete piece of information with an associated difficulty class. (In practice, it looks very similar to a Gather Information table.)
Note that the term “network” is not necessarily being used in a literal sense, but rather as a convenient way of referring to multiple systems or accounts that are somehow meaningfully related to each other. (For example, the home computer of Sansasoft’s district manager may not be directly wired into the corporate infranet, but the e-mails on her computer could easily contain compromising information, so for the purposes of this system it would be considered part of the “Sansasoft Network”.)
TERMINALS
Terminals refer to any computer, cellphone, access point, or user account that the PCs can attempt to hack. Each terminal is rated with an access cap, an intel value, and a security modifier. Some terminals may also have special features.
Access Cap: The maximum DC that can be achieved on a Hacking check using that terminal. If a higher result is rolled, the excess is ignored. (For example, a hacker named Panda is using a terminal with an access cap of 15. Rolling her Hacking skill, she gets a result of 22. Despite that, the result of her check is treated as a 15.)
Intel Value: The intel value of the terminal determines the maximum number of entries that can be gleaned from the Network Intel Table. (For example, Panda’s DC 15 result on her Hacking check is high enough to theoretically access the first six pieces of information on the Network Intel Table. But if the system she’s using only has an intel value of 2, she’ll be limited to two pieces of information.)
Security Modifier: Modifies the skill check made to hack the system. For example, a cellphone with a -4 security modifier applies a -4 penalty to a hacker’s skill check.
TERMINAL SPECIAL FEATURES
These special features (and any others you can imagine) can be added to any terminal. In fact, a single terminal might have several special features.
Communications Control: The terminal allows monitoring and/or control of local communication channels.
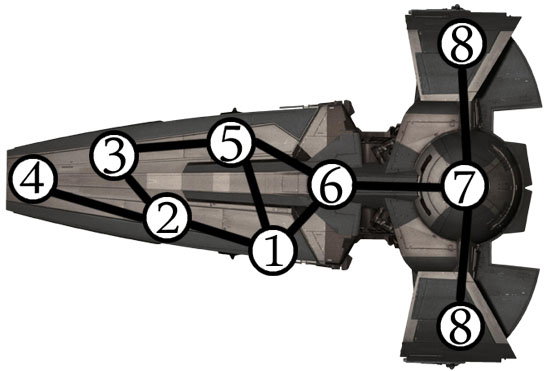
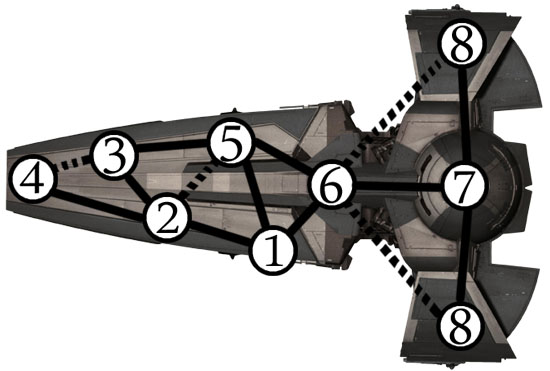
Data Tunnel: A data tunnel connects one terminal to another terminal. Each data tunnel is rated with a DC. With a successful Hacking check, a hacker can use the data tunnel to access the remote terminal. Some data tunnels might also grant bonuses when attempting to hack the remote terminal they link to.
High-Value Content: A high-value system grants a bonus to the hacker’s highest result on the Network Intel Table to date. (The more valuable the system, the higher the bonus.)
Specific Content: Although the point of this tactical hacking system is generally to avoid coding specific information to specific systems, in some circumstances it may still be valuable to do so. Specific content could also refer to security maps, data network maps, or other mission-valuable intel.
Systems Control: The terminal can be used to control surveillance cameras, robots, gun turrets, environmental controls, navigation systems, or any number of other “real world” systems.
PREP LIST
For the purposes of tactical hacking, think of each “network” as a body of related information. Each terminal on the network is a system or account which either houses part of that body of information or has access to it. It is assumed that there are a multitude of ways to discover each piece of information in the network. (For example, a hacker could discover Sansasoft’s illegal digital smuggling by reading compromising e-mails; performing forensic examinations on black book budgets; decrypting incriminating communication intercepts; discovering off-book shipping manifests; or any number of other possibilities.) If a piece of information can really only be discovered in a specific way, then that’s specific content that should be keyed as a special feature to a particular terminal.
When prepping a network for tactical hacking, you first need to prep the Network Intel Table. Here’s a sample:
| DC | Sansasoft Network Intel |
|---|---|
| 10 | Sansasoft has recently been negotiating a lot of high-value contracts with GigaGlass, a Russian manufacturer of augmented reality specs. (Statistical survey of sales invoices.) |
| 10 | The master override code for the doors in Building A is 5226. (Briefing packet for employee temporarily transferred from a different office.) |
| 15 | There have been repeated complaints regarding the quality of goods and services provided by a company called GigaGlass. Despite the problems, Sansasoft has been increasing the volume of their business with GigaGlass. (Internal memos to and from COO Deidre Brooks.) |
| 18 | Motion detectors have recently been installed in the prototyping labs on the third floor. (Billing dispute recorded in e-mails exchanged with the accounting department.) |
| 20 | VIP travel arrangements were recently made for a group of executives from the Marilyn Corporation. (Travel records filed by an administrative assistant named Leticia Moray.) |
| 24 | A keylogging worm was disseminated onto the network by a disgruntled former employee. Identifying and cleaning every system that’s been infected has proven difficult. (Detecting and exploiting the keylogger on an infected system. 1 in 4 chance of a terminal being infected; grants +1 intel value and +4 bonus to Hacking checks made on that system.) |
| 25 | Massive quantities of encrypted data are being streamed from Sansasoft-sourced GigaGlass augmented reality specs to servers being rented from the Marilyn Corporation. (Network traffic logs.) |
| 28 | There used to be a fireplace on the 8th floor. It was drywalled up in a remodel eight years ago, but its chimney would have run right past the executive suite of CEO Erik Balley on the top floor. (Approval blueprints from the remodel.) |
| 30 | Sansasoft CEO Erik Bally has recently requested that all copies – including backup copies – of e-mails sent from his office on April 30th be destroyed. Local copies have been purged, but it’s possible copies might still be found in the offline backups kept in their Sacramento offices. (E-mails from IT security.) |
(I’ve included a potential explanation for how the hacker could access each piece of information. You could expand on that by creating full handouts for each piece of information; or you could skip that and just improvise the details during play.)
Second, you need to prep a list of the terminals on the network. (Such a list could also easily be integrated into a location key or other reference as appropriate.) For example, you might stat up the customer service terminals at Sansasoft like this:
CS Terminals (access cap 15, intel value 1, security modifier +0): There is a 1 in 10 chance that any given customer service terminal will instead have no access cap (due to an unusually compromising internal e-mail). Otherwise, hackers can gain no more than 3 pieces of intel in total from all customer service terminals.
RUNNING THE SYSTEM
When a PC wants to hack a terminal, follow these steps:
(1) The character makes a Hacking check.
(2) Modify the check by the terminal’s security modifier.
(3) Check to see if the terminal’s access cap applies and reduce the effective check result if necessary.
(4) Use the character’s effective check result to determine the number of previously unrevealed pieces of information they can discover. If this number is larger than the terminal’s intel value, randomly determine which pieces of intel they receive.
Alternatively, you could randomly determine between all possible pieces of intel (which could result in them learning nothing new due to duplication from previous efforts).